How To Prevent Brute Force Attack: Safeguard Tips

Welcome to our comprehensive guide on preventing brute force attacks and safeguarding your digital assets. In this article, we will provide you with effective strategies to protect your web applications from unauthorized access and potential data breaches. By implementing secure login methods and enhancing brute force protection, you can strengthen your overall cybersecurity.
Brute force attacks have become a significant threat to online security, targeting websites, applications, and even personal accounts. These attacks involve attackers systematically guessing passwords until they find the correct one, gaining unauthorized access. It is essential to understand the risks associated with such attacks and take proactive measures to mitigate them.
In the following sections, we will dive into the details of secure login methods, brute force protection strategies, strengthening web application security, and user education. By employing these safeguard tips, you can ensure the integrity and confidentiality of your sensitive information.
Don’t let your web applications fall victim to brute force attacks. Let’s explore the steps you can take to fortify your digital defenses and keep cybercriminals at bay.
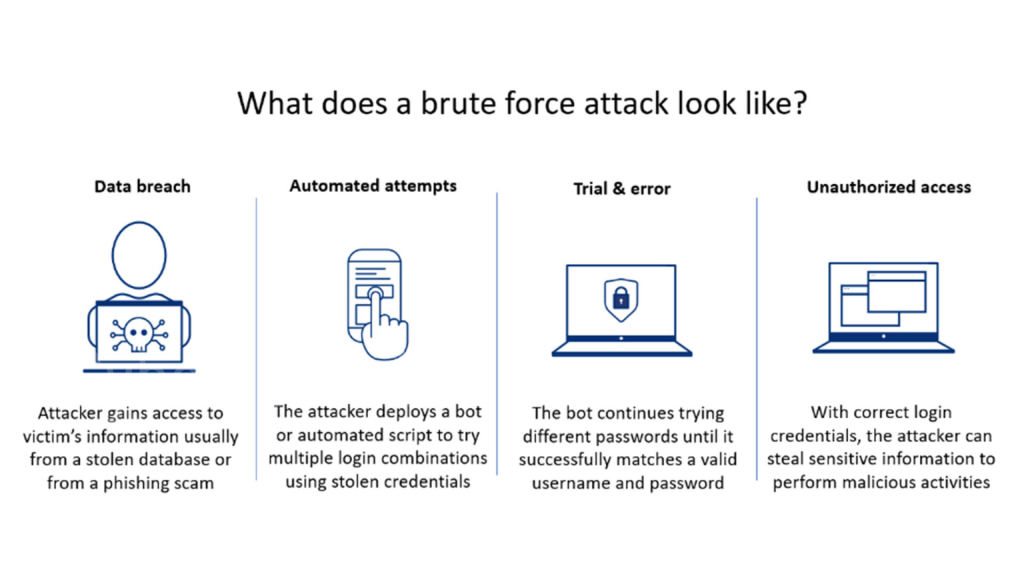
Understanding Brute Force Attacks
Before we dive into prevention strategies, it’s important to understand what a brute force attack is and how it can compromise your web application security. Brute force attacks are malicious attempts to gain unauthorized access to a system or account by systematically trying all possible combinations of passwords or encryption keys until the correct one is found. This method relies on the attacker’s persistence and automated tools to carry out thousands or even millions of login attempts in a short period.
Methods Used by Attackers
Brute force attacks commonly target login pages, such as those used for email accounts, e-commerce platforms, or content management systems. Attackers can use various techniques, such as:
- Manual attacks: Attackers manually enter different passwords or keys into login forms, relying on intuition or common patterns to guess the correct one.
- Wordlist attacks: Attackers use pre-generated lists of commonly used passwords or combinations to systematically try each one until they gain access.
- Dictionary attacks: Attackers use dictionaries or word databases to try every word or combination in the list as a password, hoping to find a match.
- Brute force software: Attackers employ automated tools, known as brute force software, to efficiently iterate through all possible combinations of characters, symbols, and numbers.
Potential Risks
Understanding the potential risks posed by brute force attacks is essential for comprehending the importance of implementing effective prevention measures. These risks include:
- Unauthorized access: Successful brute force attacks can grant attackers unauthorized access to sensitive data, personal information, or confidential documents.
- Data breaches: Brute force attacks can lead to data breaches, which can severely impact individuals or organizations, resulting in financial losses, reputational damage, or legal consequences.
- Account takeovers: By gaining access to user accounts, attackers can hijack email accounts, social media profiles, or financial platforms, posing as the account owner and engaging in malicious activities.
- Resource consumption: Brute force attacks often put a strain on servers, consuming significant amounts of processing power, memory, or network resources, potentially leading to system failures or slowdowns.
Now that we have a solid understanding of what brute force attacks are and the risks they pose, we can explore effective prevention strategies to safeguard your web application security.
Secure Login Methods
Implementing secure login methods is essential to ensure the protection of your digital assets and prevent brute force attacks. By following best practices for creating strong passwords, utilizing two-factor authentication, and implementing login rate limiting, you can significantly enhance the security of your login process.
Strong Password Guidelines
Creating strong and complex passwords is an effective way to safeguard your accounts from unauthorized access. Here are some guidelines to consider:
- Use a combination of uppercase and lowercase letters, numbers, and special characters.
- Avoid using easily guessable information like your name, birthdate, or simple words.
- Ensure your password is at least 8-12 characters long.
- Regularly update your passwords and avoid reusing them across multiple accounts.
Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your login process by requiring two different types of authentication. Typically, this involves something you know (like a password) and something you possess (like a unique code from an authentication app or a fingerprint). By enabling 2FA, even if a malicious actor obtains your password, they would still need the second factor to gain access to your account.
Login Rate Limiting
Login rate limiting is a technique to prevent brute force attacks by restricting the number of login attempts within a specified timeframe. By implementing rate limits, you can deter attackers from guessing passwords through repeated login attempts. This helps to protect against automated scripts or bots that attempt to gain unauthorized access by trying numerous combinations of usernames and passwords.
By following these secure login methods, you can significantly reduce the risk of falling victim to brute force attacks. Remember to consistently update and strengthen your password, enable two-factor authentication, and implement login rate limiting to ensure the security of your accounts and sensitive information.
Brute Force Protection Strategies
In addition to implementing secure login methods, there are other effective strategies you can employ to protect against brute force attacks. Two commonly used techniques are IP blocking strategies and captcha implementation.
IP Blocking Strategies
IP blocking is a proactive approach that involves preventing access to your website or application from specific IP addresses or IP ranges. By blocking suspicious or known malicious IP addresses, you can significantly reduce the risk of brute force attacks.
There are several IP blocking strategies you can implement:
- Blacklisting: Maintain a blacklist of IP addresses associated with known attackers. This can be done manually or through the use of threat intelligence services.
- Whitelisting: Restrict access to your website or application to only trusted IP addresses, effectively blocking all others.
- Rate Limiting: Implement rate limiting policies that restrict the number of login attempts allowed within a certain timeframe from a specific IP address. This helps prevent brute force attacks by slowing down the rate at which an attacker can guess passwords.
Captcha Implementation
Captchas are another effective tool for preventing automated brute force attacks. A captcha is a challenge-response test used to determine whether the user is human or a bot. By adding captchas to your login forms, you can ensure that only legitimate users gain access to your system.
There are different types of captchas you can implement:
- Image-based Captchas: Users are required to select certain images or identify objects within an image to prove their human identity.
- Mathematical Captchas: Users are presented with simple math problems, such as addition or subtraction, that they must solve to proceed.
- ReCaptcha: ReCaptcha is a widely used captcha service provided by Google. It utilizes advanced algorithms to differentiate between human users and bots.
By deploying both IP blocking strategies and captchas, you can enhance the security of your website or application and effectively deter brute force attacks.
Strengthening Web Application Security
Ensuring the security of your web applications is paramount in preventing brute force attacks and safeguarding your sensitive data. By following cybersecurity best practices, you can significantly enhance your web application security defenses. Let’s take a closer look at some of these practices:
- Regular software updates: Keeping your web applications updated with the latest patches and security fixes is imperative. This helps address any known vulnerabilities and minimizes the risk of brute force attacks.
- Code reviews: Conducting regular code reviews helps identify and address any potential security loopholes or weaknesses in your application’s code. This proactive approach allows you to fix vulnerabilities before they can be exploited by attackers.
- Vulnerability testing: Regularly testing your web applications for potential vulnerabilities is a crucial aspect of maintaining robust security. By employing tools and techniques to identify and remediate vulnerabilities, you can significantly reduce the risk of brute force attacks.
By implementing these cybersecurity best practices, you can mitigate the risks of brute force attacks and enhance the overall security posture of your web applications. Remember, a proactive approach to security is key to staying one step ahead of potential attackers.
Educating Users on Security Measures
One of the most important factors in preventing brute force attacks is user education. By informing and empowering your users to follow cybersecurity best practices, you can significantly reduce the risk of successful attacks.
Guidelines for Creating Strong Passwords
Strong password guidelines are essential to protect user accounts from unauthorized access. Educate your users on the importance of creating complex passwords that are difficult to guess and resistant to brute force attacks. Encourage them to include a combination of uppercase and lowercase letters, numbers, and special characters in their passwords. Additionally, emphasize the importance of avoiding common words, personal information, and easily guessable patterns.
Recognizing Potential Phishing Attempts
Another crucial aspect of user education is teaching your users how to identify and avoid phishing attempts. Phishing attacks often rely on social engineering techniques to trick users into revealing their login credentials or sensitive information. Provide guidance on how to recognize suspicious emails, links, and attachments. Teach users to double-check the sender’s email address, look for grammatical errors or inconsistencies in the message, and never share personal information or login credentials through email or unfamiliar websites.
By continuously educating your users on these cybersecurity best practices, you can create a security-conscious environment and reduce the likelihood of successful brute force attacks.
Conclusion
Brute force attacks pose a significant threat to your digital assets, but there are proactive measures you can take to prevent such attacks and safeguard your sensitive data. By implementing secure login methods, utilizing brute force protection strategies, strengthening web application security, and educating users, you can establish a robust defense against brute force attacks.
One of the fundamental steps in preventing brute force attacks is to implement secure login methods. This includes following strong password guidelines, encouraging the use of two-factor authentication, and implementing login rate limiting. By ensuring that users create strong passwords and providing an additional layer of authentication, you significantly reduce the vulnerability to brute force attacks.
In addition to secure login methods, employing brute force protection strategies can further enhance your defenses. IP blocking strategies help to block suspicious IP addresses known for malicious activities, while captchas serve as a deterrent for automated brute force attacks. By incorporating these measures, you can complicate the attack process, making it more challenging for attackers to gain unauthorized access.
Strengthening web application security is another essential aspect of preventing brute force attacks. Regular software updates, code reviews, and vulnerability testing are necessary to detect and patch any potential security vulnerabilities. By staying proactive in keeping your applications up to date, you minimize the opportunities for attackers to exploit known weaknesses.
Lastly, educating users on security measures is crucial to overall defense against brute force attacks. By providing clear guidelines for creating strong passwords and raising awareness about potential phishing attempts, you empower users to take an active role in protecting their accounts. Educating users about the risks and best practices establishes a culture of security consciousness, further bolstering your defenses.
In conclusion, by implementing secure login methods, utilizing brute force protection strategies, strengthening web application security, and educating users, you can effectively prevent brute force attacks. These safeguard tips will enhance your cybersecurity posture and ensure the safety of your valuable data. Stay vigilant, stay informed, and protect your digital assets from brute force attacks.
FAQ
What is a brute force attack?
A brute force attack is a hacking technique where an attacker tries multiple combinations of usernames and passwords to gain unauthorized access to a system or account. This method relies on the attacker systematically guessing all possible combinations until the correct one is found.
How can I prevent brute force attacks?
There are several effective strategies to prevent brute force attacks. Firstly, ensure you have strong and unique passwords for all your accounts. Enable two-factor authentication whenever possible to add an extra layer of security. Additionally, implementing login rate limiting can restrict the number of login attempts an attacker can make. Regularly updating your software and educating users about cybersecurity best practices are also essential preventive measures.
What are secure login methods?
Secure login methods are measures implemented to enhance login security and prevent brute force attacks. Some examples include creating strong passwords that combine uppercase and lowercase letters, numbers, and special characters. Two-factor authentication adds an extra layer of verification by requiring users to provide an additional code or token. Login rate limiting restricts the number of login attempts made within a certain timeframe, making it harder for attackers to guess the correct credentials.
How can IP blocking protect against brute force attacks?
IP blocking is a strategy where certain IP addresses or ranges are prevented from accessing a system or application. This can be an effective way to prevent brute force attacks as it restricts access to potential attackers. By identifying and blocking IP addresses known to be associated with malicious activities, you can significantly reduce the risk of unauthorized access.
What is the role of captchas in preventing brute force attacks?
Captchas are security measures that require users to complete a challenge to prove they are human. They are designed to distinguish between genuine users and automated bots. Implementing captchas can help prevent automated brute force attacks by adding an additional layer of protection. Captchas typically require users to solve puzzles or enter a code displayed in an image, which automated bots find difficult to bypass.
How can I strengthen web application security?
Strengthening web application security involves following cybersecurity best practices. Regularly updating your application and its components, performing code reviews to identify potential vulnerabilities, and conducting regular vulnerability testing are essential steps. By staying up to date with the latest security patches and continuously monitoring your application for potential weaknesses, you can enhance its overall security and reduce the risk of successful brute force attacks.
How can I educate users about security measures?
Educating users about security measures is crucial in preventing brute force attacks. Provide clear guidelines on creating strong and unique passwords, encourage them to enable two-factor authentication, and teach them how to recognize potential phishing attempts. Regularly communicate with your users through newsletters, blog posts, or educational videos to keep them informed about the latest cybersecurity best practices.
