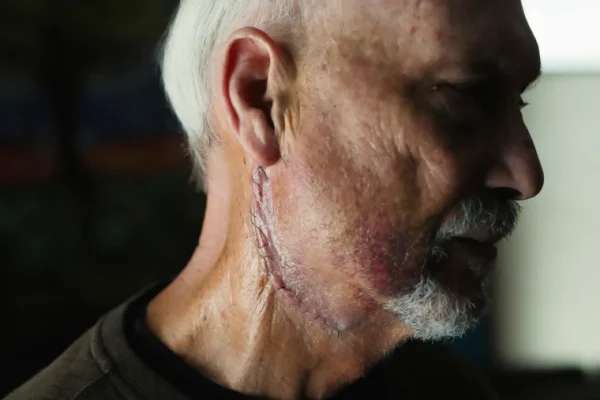Broken bones, burning eyes: How Trump’s DHS deploys ‘less lethal’ weapons on protesters
Broken bones, burning eyes: How Trump’s DHS deploys ‘less lethal’ weapons on protesters Tactics of Enforcement Federal agents have deployed rubber bullets and pepper spray…