Welcome to our article on brute force attacks – a common and alarming cybersecurity threat that individuals and organizations must be aware of. In this section, we will define what a brute force attack is and provide examples to help you understand its mechanics. Let’s dive in! So, what exactly is a brute force attack? Simply put, it is a hacking method where an attacker tries every possible combination of passwords or encryption keys until they find the correct one. This could mean thousands or even millions of attempts, depending on the complexity of the password. The aim is to gain unauthorized access to a system, compromising its security and potentially causing significant damage along the way. To further illustrate, let’s consider an example. Imagine a hacker attempting to break into an email account by systematically trying different combinations of passwords until the correct one is found. Each attempt is made rapidly and automatically until success is achieved. This relentless and methodical approach characterizes the nature of brute force attacks. Brute force attacks pose a significant threat to individuals and organizations alike. If successful, these attacks can lead to various security breaches, such as unauthorized access to sensitive data, financial loss, identity theft, and even the hijacking of entire systems. The implications are far-reaching and often devastating. It is crucial to understand the mechanics and potential threats of brute force attacks to effectively safeguard against them. In the following sections, we will explore the various techniques used in brute forcing, types of attacks, and how to prevent them. By staying informed and implementing preventive measures, you can minimize the risk and protect yourself from the damaging consequences of brute force attacks. Understanding Brute Force Attacks In this section, we will delve deeper into the mechanics of brute force attacks. Understanding how attackers exploit vulnerabilities through brute forcing techniques is essential in strengthening your security systems. Let’s explore the different types of brute force attacks and the techniques employed by malicious actors. Types of Brute Force Attacks Brute force attacks manifest in various forms, each targeting different aspects of an individual or organization’s security. These attacks can include: User Account Breach: Attackers attempt to gain unauthorized access to user accounts by systematically guessing the correct combination of usernames and passwords. Network Service Attack: Attackers bombard network services (such as email or FTP servers) with multiple login attempts, hoping to break through weak authentication mechanisms. Web Application Attack: Attackers target web applications by submitting numerous combinations of login credentials, attempting to find a vulnerability that grants unauthorized access. Brute Forcing Techniques Brute forcing techniques refer to the methods employed by attackers to crack security measures. Some commonly used techniques include: Dictionary Attacks: Attackers use a pre-compiled list of commonly used passwords or words to systematically guess the correct combination. Hybrid Attacks: Attackers combine dictionary attack methods with variations such as adding numbers, special characters, or substituting letters. Incremental Attacks: Attackers start with a basic password and systematically generate variations by adding numbers, letters, or special characters. By becoming familiar with the types of brute force attacks and the techniques used, you can better assess the vulnerabilities present in your systems and take appropriate preventive measures. Potential Threats of Brute Force Attacks In today’s interconnected digital landscape, the potential threats posed by brute force attacks are a growing concern for both individuals and organizations. Such attacks can compromise security and lead to severe consequences for their victims. Understanding these risks is crucial in order to take effective preventive measures. A successful brute force attack can result in various potential threats, including: Unauthorized Access: Brute force attacks can grant unauthorized individuals or malicious actors access to sensitive data, systems, or accounts. This unauthorized access can lead to data breaches, financial loss, or even identity theft. Account Takeover: By uncovering weak passwords through repetitive login attempts, attackers can gain control of user accounts. This can result in unauthorized actions, such as sending malicious emails, making unauthorized transactions, or spreading malware. Network Compromise: Brute force attacks can compromise an organization’s entire network by exploiting vulnerabilities in devices, servers, or applications. This can lead to the theft or destruction of critical data, disruption of operations, and damage to reputation. Resource Exhaustion: Brute force attacks involve a large number of login attempts, which can overwhelm servers and network resources. This can result in denial-of-service (DoS) attacks, causing system downtime, loss of productivity, and customer dissatisfaction. It is crucial to note that the consequences of a successful brute force attack can extend beyond immediate financial or operational impact. Organizations may suffer long-term damage to their brand reputation, loss of customer trust, and potential legal consequences. To mitigate these potential threats and protect against brute force attacks, individuals and organizations must prioritize implementing robust security measures and adopting best practices. By doing so, they can prevent unauthorized access, defend against account takeovers, safeguard their networks, and ensure the integrity of their digital presence. Preventing Brute Force Attacks Preventing brute force attacks is crucial for safeguarding your personal and organizational security. By implementing proactive measures, you can significantly reduce the risk of falling victim to these malicious attacks. One of the most effective strategies is to emphasize the importance of strong, complex, and unique passwords. Using strong passwords is essential in preventing brute force attacks. A strong password should be at least 12 characters long and contain a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using predictable patterns or easily guessable information, such as your name, birthdate, or favorite sports team. In addition to strong passwords, consider utilizing two-factor authentication (2FA) whenever possible. This adds an extra layer of security by requiring a secondary verification method, such as a code sent to your mobile device, in addition to your password. 2FA significantly reduces the risk of unauthorized access even if an attacker manages to crack your password. Regularly updating your passwords is also crucial in preventing brute force attacks. Avoid reusing passwords across multiple accounts as
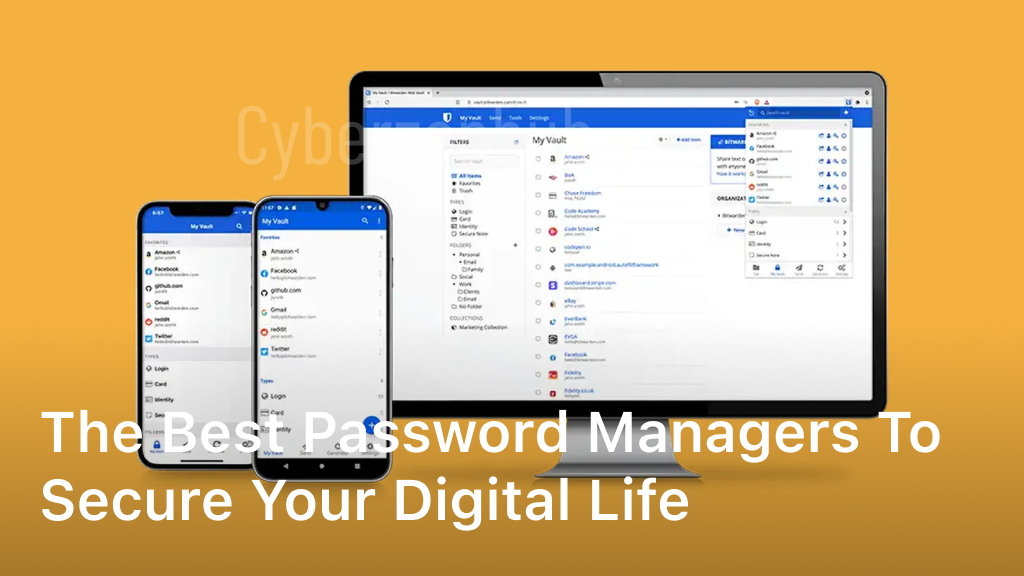
The Best Password Managers to Secure Your Digital Life
In today’s digital age, it’s essential to protect your online accounts and personal information with a secure password manager. With a variety of options available on the market, finding the best Android password manager that offers both security and convenience can be a daunting task. In this article, we will explore the top-rated password managers for Android devices, comparing their features and providing recommendations to help you find the perfect solution to safeguard your digital world. Understanding the Importance of Android Password Managers. Before we dive into the best Android password managers, let’s first understand the importance of using such a tool. Password managers not only store your passwords securely but also generate strong and unique passwords for each of your accounts. They simplify the login process, eliminate the need to remember multiple passwords, and protect against common security risks like phishing attacks and data breaches. In this section, we will analyze password manager app reviews, compare different features offered by various password managers, and highlight the key factors to consider when choosing the right one for your Android device. Why You Need Password Manager App Reviews With a plethora of password managers available in the market, it can be overwhelming to decide which one to choose. That’s where password manager app reviews come in handy. These reviews provide insights into the performance, user experience, and overall satisfaction of existing users. By reading reviews from real users, you can get a better understanding of the strengths and weaknesses of different password managers, helping you make an informed choice. Look for reviews that specifically mention key features such as encryption strength, ease of use, and compatibility with Android devices. Comparing Password Manager Features When choosing an Android password manager, it’s crucial to consider the features offered by different providers. Some important features to look out for include: Secure password storage and encryption Password generator to create strong and unique passwords Autofill functionality for seamless login experiences Biometric authentication options like fingerprint or face recognition Password sharing capabilities By comparing these features, you can determine which password manager aligns with your specific needs and preferences. Password Manager Secure Password Storage Password Generator Autofill Biometric Authentication Password Sharing Provider A Yes Yes Yes Fingerprint Yes Provider B Yes Yes Yes Fingerprint, Face Recognition No Provider C Yes No Yes No No Table: Comparison of password manager features As seen in the table above, different password managers offer varying features. Consider your priorities and choose the one that best meets your requirements. Top-Rated Android Password Managers: A Comprehensive Review. In this section, we will explore the top-rated Android password managers currently available in the market. When it comes to protecting your online accounts and personal information, choosing the right password manager is crucial. With a plethora of options to choose from, it can be overwhelming to find the best one for your Android device. We will evaluate these password managers based on their security features, ease of use, compatibility with Android devices, and additional functionalities. Whether you’re looking for the best free password manager for Android or the most feature-rich option, this comprehensive review will help you make an informed decision. Security Features When it comes to password managers, security is of utmost importance. We will analyze the encryption algorithms used, the ability to generate strong and unique passwords, and the options for two-factor authentication. Ease of Use An intuitive and user-friendly interface is essential for a seamless password management experience. We will assess the simplicity of these Android password managers, including features like autofill, password capture, and easy organization of login credentials. Compatibility with Android Devices Since we are focusing on Android password managers, compatibility with different Android versions and devices is a crucial factor. We will explore these managers’ compatibility and their ability to sync across multiple devices for easy access. Additional Functionalities Some password managers offer additional features like password sharing, password strength analysis, and secure notes. We will examine these additional functionalities and how they enhance the overall password management experience. By the end of this section, you will have a comprehensive understanding of the top-rated Android password managers available and be equipped with the knowledge to choose the best one for your needs. Recommendations for the Best Android Password Manager. After conducting a comprehensive review of various Android password managers, we have carefully evaluated their features and performance to provide you with our top recommendations. These selections strike the perfect balance between security, convenience, and user experience. Whether you are an individual user or managing passwords for a team, these password managers will meet your requirements for effectively safeguarding your digital life. 1. LastPass LastPass is a leading password manager known for its robust security features and user-friendly interface. It offers strong encryption technology and multi-factor authentication options for enhanced protection. LastPass also allows seamless syncing across multiple devices and has a password sharing feature that simplifies teamwork while keeping sensitive information secure. 2. Dashlane Dashlane is another top-notch password manager that stands out for its sleek design and advanced security measures. It offers biometric authentication, such as fingerprint and face recognition, ensuring quick and secure access to your passwords. Dashlane’s automatic password changer feature also efficiently updates your passwords across different platforms, saving you time and effort. 3. 1Password 1Password is a popular choice for individuals and businesses alike. It offers a seamless user experience with its intuitive interface and convenient features. 1Password provides strong encryption, supports biometric authentication, and includes a secure password generator. Additionally, it enables secure sharing of passwords and other sensitive information with trusted individuals or team members. Password Manager Encryption Strength Cross-Platform Compatibility Biometric Authentication Password Sharing LastPass High Yes Yes Yes Dashlane High Yes Yes No (Paid version) 1Password High Yes Yes Yes These three Android password managers have consistently received positive user reviews and have proven to be reliable in terms of security and functionality. Choose the one that best suits your needs and enjoy enhanced password security and convenience
5 Types of Password Attacks & How to Stop Them
Welcome to our article on the various types of password attacks that pose a threat to your online security. In today’s digital landscape, ensuring the protection of your passwords is more crucial than ever. Cybercriminals are constantly evolving their tactics, employing ingenious methods to gain unauthorized access to your accounts. That’s why it’s essential to stay informed and learn how to safeguard your passwords effectively. In this article, we will delve into the five most prevalent types of password attacks that you should be aware of. By understanding these attacks and implementing the recommended measures, you can significantly enhance your online security posture and protect your valuable information. Phishing Attacks Phishing attacks are one of the most common and deceptive methods used by cybercriminals to steal sensitive information, including passwords. These attacks involve tricking users into disclosing their login credentials through deceptive techniques and false pretenses. Attackers often masquerade as trusted entities, such as banks, social media platforms, or online retailers, making it difficult for users to identify the malicious intent behind their messages. They employ various techniques to exploit human psychology and manipulate users into divulging their passwords. Spoofed Websites: Attackers create websites that closely resemble legitimate websites to trick users into entering their login credentials. These fake websites typically have URLs that are slightly different from the genuine ones, making it challenging to detect the deception. Phishing Emails: Attackers send emails pretending to be from reputable organizations, enticing users to click on malicious links or download attachments. These emails often contain urgent or enticing messages that instigate immediate action. Social Engineering: Attackers use psychological manipulation techniques, such as creating a sense of urgency or exploiting emotions, to convince users to disclose their passwords. They may impersonate authority figures or present plausible scenarios to gain the victim’s trust. Identifying phishing attacks requires vigilance and suspicion. Here are some tips to help users avoid falling victim to these deceptive schemes: Look for suspicious or misspelled URLs in emails and websites. Verify the authenticity of emails and messages by contacting the organization directly through official channels. Avoid clicking on links or downloading attachments from unknown or suspicious sources. Be cautious of emails or messages that create a sense of urgency or demand immediate action. Regularly update and use reputable antivirus software and security measures. By staying informed and practicing caution, users can protect themselves against phishing attacks and safeguard their passwords and sensitive information. Phishing Attack Techniques Examples Spoofed Websites Creating a fake banking website identical to the legitimate one to steal user credentials. Phishing Emails Sending an email claiming to be from a popular social media platform, requesting users to verify their account details by clicking on a link. Social Engineering Pretending to be a tech support representative and asking users to provide their passwords to resolve a fake issue. Credential Stuffing Attacks Credential stuffing attacks are a type of cyber attack where attackers use leaked login credentials from one website to gain unauthorized access to user accounts on other websites. Unlike phishing attacks that rely on tricking users into revealing their passwords, credential stuffing attacks exploit the reuse of passwords across different platforms. The process of carrying out a credential stuffing attack involves using automated scripts or bots that systematically input stolen usernames and passwords into login forms on various websites until a successful match is found. This method takes advantage of the fact that many individuals use the same password for multiple online accounts. Once a match is found, the attacker can access the compromised user account to carry out further malicious activities. To protect yourself against credential stuffing attacks, it is crucial to follow good password hygiene practices. The first step is to ensure that you have unique passwords for each of your online accounts. This prevents attackers from gaining access to multiple accounts even if one set of credentials is compromised. Furthermore, consider using a password manager to generate strong and complex passwords that are difficult for attackers to crack. A password manager also helps you remember and securely store your passwords, reducing the temptation to reuse them. Enabling multi-factor authentication (MFA) adds an extra layer of security to your accounts. With MFA, even if an attacker obtains your username and password, they would still need an additional authentication factor, such as a unique code sent to your mobile device, to gain access to your account. By implementing these precautions, you can significantly reduce the risk of falling victim to credential stuffing attacks and safeguard your personal information across various online platforms. Brute Force and Dictionary Attacks In the realm of password attacks, two common techniques used by hackers are brute force attacks and dictionary attacks. While they have similar end goals – cracking passwords to gain unauthorized access – their methods differ significantly. Brute Force Attacks Brute force attacks involve systematically trying every possible password combination until the correct one is found. This method relies on the attacker’s ability to guess the password by testing all possible combinations of characters. It can be a time-consuming process, especially for longer and more complex passwords. Attackers employ automated software or scripts that iterate through different character combinations, starting with simple ones and gradually increasing complexity. This approach exploits the vulnerabilities associated with weak or easily guessable passwords. Dictionary Attacks On the other hand, dictionary attacks utilize pre-existing wordlists to crack passwords. These wordlists contain commonly used passwords, well-known phrases, and combinations derived from previous data breaches. By comparing the passwords in the wordlist with the target account’s password, attackers can identify a match and gain unauthorized access. Dictionary attacks are often more effective than brute force attacks since they rely on the widespread usage of weak and easily guessable passwords. Additionally, attackers can augment their wordlists with personal information about the target, such as their name or birthdate, to increase the chances of a successful attack. Preventing Brute Force and Dictionary Attacks To protect yourself from brute force and dictionary attacks, it is crucial to create
Are Password Managers Safe? Security Insights
Welcome to our in-depth exploration of password managers and their security features. In this article, we will address the question on everyone’s mind: Are password managers safe? In today’s digital age, where online security is paramount, using a password manager has become a popular choice for individuals and businesses alike. These powerful tools offer a secure and convenient way to manage your passwords and protect your online credentials. Throughout this article, we will provide valuable insights into the safety of password managers. We will discuss their benefits, the features they offer, and the encryption standards they use to safeguard your data. By the end, you’ll have a comprehensive understanding of password manager security and the reassurance you need to keep your online presence protected. So, let’s dive in and explore the world of password managers together! Benefits of Password Managers Using a password manager offers a multitude of benefits, making it an essential tool for secure password management. Let’s explore some key advantages: Convenience: With a password manager, you no longer need to remember multiple complex passwords. It securely stores all your passwords in one place, eliminating the need for manual entry and tedious password retrieval. Strong and Unique Passwords: Password managers generate strong, random passwords that are unique to each website or application. This ensures that even if one account is compromised, your other accounts remain unaffected. By creating and managing complex passwords automatically, password managers enhance your online security. Secure Password Management: Password managers simplify the process of securely managing your passwords. They provide a secure vault where you can store passwords, credit card details, and other sensitive information. This encrypted vault is protected by a master password, ensuring only you have access to your data. Password Manager Benefits Comparison Benefits Traditional Password Management Password Manager Convenience Highly inconvenient and prone to forgetting passwords Centralized storage and autofill functionality for easy access Password Strength Relies on weak, easily memorable passwords Generates strong, complex passwords for enhanced security Security Potential for password reuse and vulnerability to hacking Encrypted storage with master password protection To fully experience the benefits of password managers, it is important to choose a trusted and reputable solution that aligns with your specific needs. By utilizing a password manager, you can enjoy the convenience, security, and peace of mind that comes with effective password management. Understanding Password Manager Features Password managers offer a range of features that enhance password security and simplify the management process. Let’s explore some of the key features that make password managers a valuable tool for online security: Autofill One of the standout features of password managers is autofill. With autofill, you no longer need to manually enter your usernames and passwords every time you visit a website or application. Password managers securely store your login credentials and automatically fill them in for you, saving both time and effort. Password Synchronization Password synchronization is another essential feature offered by password managers. With this feature, you can access your passwords from multiple devices seamlessly. Whether you’re using a desktop computer, laptop, or mobile device, password synchronization ensures that your passwords are always up-to-date and accessible wherever you go. Secure Password Sharing Sharing passwords securely with other users is made simple with password managers. Instead of sending sensitive login information via unsecured methods, password managers allow you to share passwords securely with trusted individuals. This feature is particularly useful for teams or families who need to share access to various accounts while maintaining utmost security. Master Password The importance of having a strong and unique master password cannot be overstated. A master password is like the key that unlocks all of your stored passwords within the password manager. It is crucial to choose a master password that is complex, memorable only to you, and resistant to brute force attacks. The master password feature ensures that even if someone gains unauthorized access to your password manager, they cannot access your stored passwords without the master password. Password Manager Encryption Standards When it comes to secure password management, one of the key factors to consider is the encryption standards employed by password managers. These encryption protocols ensure that your sensitive data is protected from unauthorized access and potential breaches. Password managers use strong encryption algorithms to scramble your passwords and other confidential information. These algorithms make it extremely difficult, if not impossible, for hackers to decipher your data even if they gain unauthorized access to it. One of the crucial encryption features to look for in a password manager is end-to-end encryption. This means that your data is encrypted on your device before it leaves your possession and remains encrypted throughout its transmission and storage. With end-to-end encryption, your passwords and other personal information are protected at every step of the process. Additionally, password managers employ various encryption methods to ensure the security of your data. These methods include hashing, salting, and key derivation functions, which add an extra layer of protection to your passwords. By using password manager encryption standards, you can rest assured that your sensitive information is shielded from potential threats. These encryption protocols make it significantly more challenging for cybercriminals to intercept and misuse your passwords, providing you with peace of mind and a higher level of online security. Conclusion In conclusion, password managers offer a reliable solution for securely storing and managing your passwords. Throughout this article, we have discussed the safety and security features of password managers, highlighting their importance in enhancing your online security. With password manager reliability, you can rest assured that your passwords are safely encrypted and protected from prying eyes. These tools offer convenience by generating strong and unique passwords, simplifying the process of secure password management. By using a password manager, you can enjoy the benefits of features such as autofill, password synchronization, and secure password sharing. Additionally, a strong master password adds an extra layer of security to safeguard your data. In today’s digital age, where cyber threats and data breaches are prevalent, relying on a
What Is Password Attack and How To Prevent
Welcome to our article on password attacks and how to effectively prevent them. In this informative piece, we will delve into the world of password attacks, discuss the various methods employed by attackers, and equip you with the knowledge needed to safeguard your personal information and online accounts. With the increasing reliance on digital platforms for various aspects of our lives, including banking, shopping, and social interactions, the security of our passwords has become more critical than ever. Hackers and cybercriminals are constantly looking for vulnerabilities to exploit, making it essential for us to stay one step ahead and protect ourselves from unauthorized access. We will explore the most common password attack methods used by attackers, such as brute force attacks, dictionary attacks, phishing attacks, and even lesser-known techniques like shoulder surfing. By understanding these methods, you will be better equipped to identify and thwart potential threats. Prevention is key when it comes to password attacks, and throughout this article, we will provide you with practical tips and best practices to strengthen your defenses. From creating strong and unique passwords to enabling multi-factor authentication, we’ll share valuable insights to help you protect your accounts and personal information. So, if you’re ready to learn about password attacks, their prevention, and common password attack methods, let’s dive in and empower ourselves with the knowledge needed to keep our digital lives secure! Understanding Password Attacks When it comes to securing our online accounts, understanding the different types of password attacks is essential. In this section, we will explore three common methods that attackers employ to gain unauthorized access to sensitive information: brute force attacks, dictionary attacks, and password cracking. Brute Force Attacks Brute force attacks occur when an attacker systematically attempts all possible combinations of passwords until they find the correct one. This method can be time-consuming, as it involves trying numerous combinations. However, with the help of powerful computers and advanced hacking tools, attackers can speed up the process of cracking passwords. Implementing strong passwords and using account lockout policies can help protect against brute force attacks. Dictionary Attacks Dictionary attacks involve using pre-compiled lists of commonly used passwords to try and gain unauthorized access. Attackers utilize these comprehensive password dictionaries, which contain words, names, and commonly used phrases, to systematically guess a user’s password. To safeguard against dictionary attacks, it is crucial to use complex and unique passwords that cannot be easily guessed. Password Cracking Password cracking is a technique where attackers use powerful software and algorithms to decrypt hashed passwords. By decrypting the hashed passwords, attackers gain access to the original password and can use it to infiltrate user accounts. To protect against password cracking, it is vital to use strong encryption algorithms and regularly update passwords with unique combinations of letters, numbers, and symbols. Attackers may also utilize guessing techniques to gain access to passwords. They might try commonly used passwords, predictable patterns, or information related to the user, such as names, birthdates, or favorite sports teams. To prevent falling victim to password guessing, it is crucial to create strong and unique passwords that are not easily associated with personal information. By understanding the various types of password attacks, including brute force attacks, dictionary attacks, and password cracking, you can take proactive steps to protect your online accounts and personal information. Brute Force Attacks One of the most common methods used by hackers to gain unauthorized access to accounts is through brute force attacks. These attacks involve an attacker systematically attempting all possible combinations of passwords until they find the correct one. The potential impact of a successful brute force attack can be severe, as it grants the attacker complete control over the compromised account, leaving personal information and sensitive data at risk. To prevent brute force attacks and ensure the security of your passwords, it is crucial to follow some effective prevention strategies: Create strong, complex passwords: Use a combination of uppercase and lowercase letters, numbers, and special characters to make your password harder to crack. Use long passwords: The longer the password, the more difficult it is to guess. Aim for a minimum of 12 characters. Use unique passwords for each account: Avoid using the same password for multiple accounts to minimize the impact of a potential data breach. Implement account lockouts and rate limiting: Set up mechanisms that lock an account or enforce a delay after a certain number of failed login attempts. Enable two-factor authentication (2FA): 2FA provides an additional layer of security by requiring a second verification step, such as a unique code sent to your mobile device, along with your password. By following these preventive measures, you can significantly reduce the risk of falling victim to brute force attacks and enhance the overall security of your online accounts. Dictionary Attacks In the world of password attacks, dictionary attacks are a popular method used by cybercriminals to gain unauthorized access to accounts. In a dictionary attack, attackers rely on a pre-compiled list of commonly used passwords, known as a dictionary, to systematically try various combinations until they find the correct password. Unlike brute force attacks that attempt all possible combinations, dictionary attacks are more efficient as they focus on commonly used passwords. Cybercriminals exploit the fact that many people use easily guessable passwords such as “password123” or “qwerty”. By using a dictionary attack, attackers can quickly identify weak passwords and gain access to sensitive information. So, how can you protect yourself against dictionary attacks? Here are some preventive measures: Use Strong and Unique Passwords: Create strong passwords that include a combination of upper and lowercase letters, numbers, and special characters. Avoid using predictable passwords like birthdays, pet names, or common words. Enable Multi-Factor Authentication: Implement multi-factor authentication whenever possible. This adds an extra layer of security by requiring users to provide additional verification, such as a unique code sent to their mobile device, in addition to their password. Regularly Update Passwords: Regularly change your passwords for different online accounts to reduce the risk of compromised credentials. Avoid using the same password
Top 5 Most Common Online Scams and How to Avoid Them
Welcome to our comprehensive guide on the top 5 most common online scams that internet users encounter. In today’s digital landscape, where scams and internet fraud are rampant, it’s crucial to stay informed and protect yourself from falling victim to these deceitful tactics. Whether it’s phishing scams, identity theft, romance scams, email scams, ransomware attacks, investment scams, lottery scams, or online shopping scams, we’ve got you covered. Throughout this article, we will discuss each of these scams in detail, providing you with an overview of how they work and the warning signs to watch out for. We will also equip you with effective strategies to safeguard yourself from becoming an easy target for online fraudsters. By understanding the mechanics of these scams and arming yourself with knowledge, you can confidently navigate the online world and protect your personal and financial information. Don’t let scammers take advantage of you; stay one step ahead with our expert advice and tips. Debt Collection Scams Debt collection scams are a common form of online fraud where scammers pose as legitimate debt collectors to extort money from innocent individuals. Understanding how these scams work and learning how to identify them can help protect you from becoming a victim of this type of fraud. How Debt Collection Scams Work Fraudsters typically contact their targets through phone calls, emails, or even text messages, claiming to be debt collectors. They use various techniques to create a sense of urgency and fear, often threatening legal action or consequences if payment is not made immediately. Scammers may provide fake documentation or personal information to convince their victims that the debt is legitimate. They usually demand payment through unconventional methods, such as wire transfers, prepaid cards, or cryptocurrency, making it difficult to trace and recover the funds. In some cases, scammers may even attempt to collect on debts that have already been paid or have expired under the statute of limitations. Signs of Debt Collection Scams Request for immediate payment without providing sufficient details regarding the debt or its origin. Threats of arrest, legal action, or loss of personal assets if payment is not made promptly. Refusal to provide written documentation or proof of the debt upon request. Demand for payment using unconventional methods, such as wire transfers or prepaid cards. Attempts to collect on a debt that you don’t recognize, have already paid, or is past the statute of limitations. Protecting Yourself from Debt Collection Scams Be wary of unsolicited calls, emails, or text messages demanding immediate payment for a debt. Verify the legitimacy of the debt by requesting written documentation and contacting the original creditor directly. Avoid providing personal or financial information to anyone you are unsure of. Do not make payments using unconventional methods requested by the debt collector. Report any suspicious or fraudulent activity to your local law enforcement and the Federal Trade Commission (FTC). Money Transfer or Mobile Payment Services Fraud Online scammers often prey on unsuspecting victims by exploiting money transfer or mobile payment services. These fraudsters employ various tactics to trick individuals into providing their financial information, leading to money transfer scams, mobile payment scams, and online payment fraud. Tactics used by fraudsters: Phishing emails and text messages that appear to be from legitimate money transfer or mobile payment service providers. Fake websites or mobile apps that resemble genuine platforms, designed to steal users’ login credentials and financial details. Social engineering techniques to manipulate victims into disclosing sensitive information or performing unauthorized transactions. Recognizing and avoiding scams: Always verify the legitimacy of the money transfer or mobile payment service provider before sharing personal or financial information. Be cautious of unsolicited communications and avoid clicking on suspicious links or downloading attachments. Double-check the website or app URL to ensure it matches the official website or app of the service provider. Set up two-factor authentication and regularly review your transaction history to detect any unauthorized activity. Only use secure and trusted payment platforms for online transactions. Protecting your financial information: Keep your personal and financial information confidential and avoid sharing it with unknown individuals or websites. Use strong, unique passwords for your money transfer or mobile payment accounts and change them regularly. Regularly update your devices and payment apps with the latest security patches and software updates. Monitor your bank and credit card statements closely for any suspicious transactions. If you suspect a scam or fraudulent activity, report it to the appropriate authorities and the money transfer or mobile payment service provider. By staying vigilant and following these precautions, you can avoid falling victim to money transfer scams, mobile payment scams, and online payment fraud. Protect your financial information and keep scammers at bay. Cryptocurrency Scams With the rise in popularity of cryptocurrency, it’s important to be aware of the potential risks associated with it. Cryptocurrency scams have become increasingly prevalent in recent years, targeting unsuspecting individuals who are drawn to the allure of digital currencies. In this section, we will explore the different types of cryptocurrency scams, highlight some red flags to watch out for, and provide essential precautions to take when dealing with digital currencies. Types of Cryptocurrency Scams: Ponzi Schemes: Scammers promise high returns on investments in cryptocurrencies, while using funds from new investors to pay off earlier investors. Phishing Attacks: Fraudsters send deceptive emails or messages, posing as legitimate cryptocurrency platforms, in an attempt to trick users into revealing their private keys or login credentials. ICO (Initial Coin Offering) Scams: Scammers create fake initial coin offerings, enticing investors to contribute funds to a non-existent or fraudulent project. Fake Exchanges and Wallets: Fraudulent platforms claim to offer secure cryptocurrency exchanges or wallets, only to steal users’ funds or private information. Warning Signs: Unrealistic Promises: Be cautious of any investment opportunity that guarantees unusually high returns or promises quick profits. Unsolicited Offers: Be wary of unsolicited communication offering investment opportunities or promoting new cryptocurrencies. Lack of Regulation: Cryptocurrency scams often operate in unregulated markets, so make sure to research and verify the legitimacy