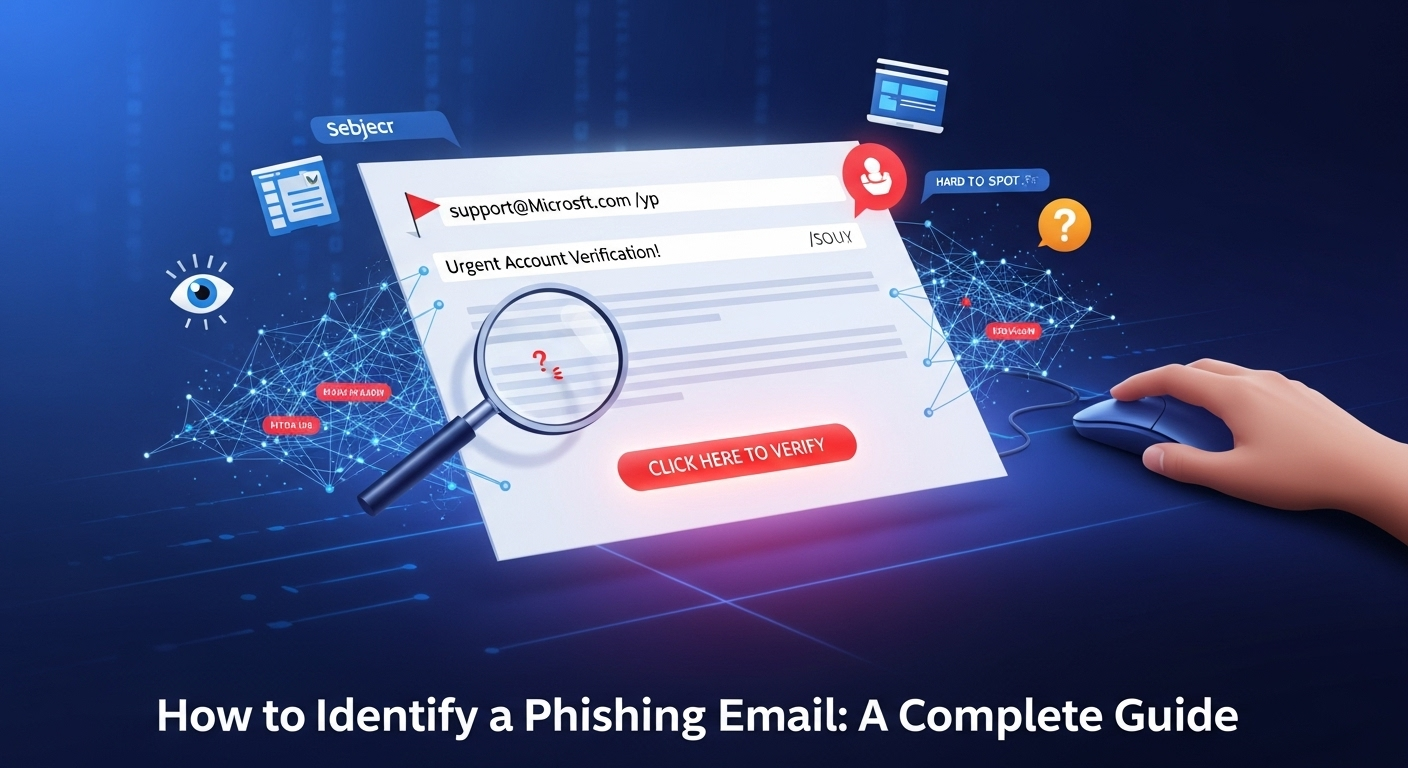
Of course. As an SEO expert, I will create a comprehensive, engaging, and SEO-optimized article that adheres to all your instructions. The content will be unique, well-structured, and designed for long-term relevance. Here is the article: In an era where our digital inboxes are a constant battleground, the threat of a single, deceptive email causing significant financial or personal damage is more real than ever. These malicious messages, known as phishing emails, are crafted by scammers to trick you into revealing sensitive information like passwords, credit card numbers, or personal details. They have become increasingly sophisticated, often perfectly mimicking legitimate communications from banks, tech companies, or even your colleagues. Understanding how to identify a phishing email is no longer just a technical skill—it is an essential life skill for navigating the modern world safely. This guide will provide you with a complete framework, from recognizing the most common red flags to understanding advanced attack methods, ensuring you can confidently protect yourself from these digital predators. What is Phishing and Why is it So Dangerous? At its core, phishing is a form of social engineering where an attacker sends a fraudulent message designed to deceive a person into revealing sensitive information. The term is a homophone of "fishing" because the attackers are essentially "fishing" for your private data in a vast sea of internet users, using a carefully crafted "lure." This lure is typically an email, but it can also be a text message (smishing) or a voice call (vishing). The ultimate goal is almost always malicious, ranging from identity theft and financial fraud to deploying ransomware on a corporate network. The danger of phishing lies in its deceptive simplicity and its psychological manipulation. Attackers exploit human trust and urgency. An email that appears to be from a familiar brand like Netflix, Amazon, or your bank can lower your guard. These emails often contain urgent calls to action, such as "Your account has been compromised, click here to secure it," or "Your payment has failed, please update your details." This manufactured sense of panic causes victims to act impulsively, bypassing the critical thinking and scrutiny they might otherwise apply. The consequences of falling for a phishing scam can be devastating. On an individual level, it can lead to drained bank accounts, fraudulent credit card charges, and full-blown identity theft, a nightmare that can take months or even years to resolve. For businesses, a single employee clicking on a phishing link can be the entry point for a catastrophic data breach. Attackers can gain access to the entire corporate network, steal proprietary data, deploy ransomware that cripples operations, and cause immense reputational and financial damage that can bring a company to its knees. The Anatomy of a Phishing Email: 7 Red Flags to Watch For While phishers are becoming more sophisticated, most fraudulent emails still contain tell-tale signs. Learning to spot these red flags is your first and most effective line of defense. By training your eye to scrutinize incoming messages, you can dramatically reduce your risk of becoming a victim. Think of it as a mental checklist you run through every time you encounter an unexpected or suspicious email. Below is a detailed breakdown of the seven most common indicators that an email is not what it seems. Some are obvious, while others are subtle, but together they form a powerful diagnostic tool. No single point is foolproof, but when you see several of them in one email, the alarm bells should be ringing loudly. Let's dissect the anatomy of a typical phishing email. 1. Scrutinize the Sender's Email Address This is one of the most reliable indicators of a phishing attempt. Attackers often try to spoof the sender's display name, which is the name you see in your inbox (e.g., "PayPal Support"). However, the underlying email address often reveals the fraud. Always take a moment to hover your mouse over or tap on the sender's name to see the full email address. Look for subtle misspellings designed to trick your brain, such as `support@paypa1.com` (using the number 1 instead of an 'l') or `service@microsft.com` (missing the 'o'). Another common tactic is using a legitimate-sounding subdomain with a non-legitimate primary domain, like `security.updates@amazon.web-login.com`. Your brain sees "amazon," but the actual domain is `web-login.com`, a random domain owned by the scammer. A real email from Amazon would come from a domain like `@amazon.com` or `@amazon.co.uk`. Never trust the display name alone; always verify the full sender address. 2. Look for Generic Salutations and Impersonal Language Legitimate companies you do business with know your name. If you receive an email from your bank, credit card company, or a service like Netflix, it will almost always address you by your first and last name (e.g., "Dear John Smith"). Phishing emails, often sent out in massive campaigns, typically use generic salutations because they don't have your personal details—that's what they're trying to get. Be highly suspicious of emails that start with vague greetings like "Dear Valued Customer," "Dear Account Holder," or simply "Greetings." While not a universal rule (some marketing emails can be generic), when a generic greeting is combined with a request for action or a warning about your account, it's a massive red flag. This impersonal approach is a classic sign that the sender is casting a wide net and hoping someone bites. 3. The Sense of Urgency or Threat This is a core psychological tactic of phishing. Attackers want to provoke an emotional reaction—fear, panic, or curiosity—to make you act before you think. They create a false sense of urgency with phrases designed to rush you into clicking a link or opening an attachment without proper scrutiny. This is a deliberate strategy to bypass your rational judgment. Common examples of these high-pressure tactics include: "Your account has been suspended due to suspicious activity. Click here to reactivate within 24 hours." "We have detected an unauthorized login attempt. Please verify your identity immediately." "Your invoice payment is overdue. Failure to pay will